I have worked with clients whose organizations were leveled by tornadoes, demolished by accidental explosions, and whose server hardware failure literally sparked catastrophe. What is clear is that, in business, you can’t afford to become complacent – tomorrow is never guaranteed.
These days, most of my career has been spent helping leaders of businesses and organizations protect themselves against a wide variety of threats in the hopes that, when danger strikes, their data is protected. In particular, I have been spending a lot of time helping protect client data from cybercriminals armed with ransomware who are looking for a chance to hijack your data to secure a quick payday. Once these hackers gain access to your network, you only have two choices: either give in to their demands or come to terms with the fact that the data is lost forever – that is, unless you have established and maintained offsite data backups as part of your disaster recover plan.
Why A Disaster Recovery Plan Is An Essential Business Tool
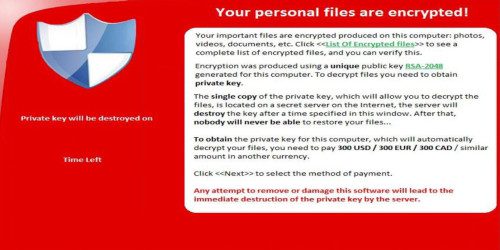
Hospitals, school districts, state and local governments, law enforcement agencies, small business, large businesses, nonprofits and every entity and organization in between are all on high alert after the FBI recently released a Ransomware Advisory. Ransomware, an insidious type of malware designed to encrypt, or lock, your valuable digital files, is being used more and more by criminals demanding money in exchange for the data’s release. Unfortunately, it has been very effective and many high-profile businesses have been successfully infiltrated.
“Too many organizations are paying ransoms to extortionist,” said cybersecurity attorney Chris Pierson in a recent article on bankinfosecurity.com. “Whether due to speed, mission criticality or lack of good backups and data proliferation, more companies are being forced to pay these days.”
Never before has it been more important for all entities, large and small, to have a plan in place to protect the network from unforeseen threats like ransomware, a fact that was reiterated by the FBI earlier this year.
Molly Halpern, host of the podcast FBI This Week, says that the ransomware threat is evolving as criminals are now focusing more on businesses, local governments and other organizations. These day’s data backups are essential.
I recommend clients to back up all their data to an offsite location located at least 2-3 miles away from the primary production area as part of the organization’s Disaster Recovery/Business Continuity Plan. Routine testing of the plan should also be conducted to ensure accuracy and completeness.
Of course, guaranteeing the validity of your data is easier said than done, which is why your best course of action is to completely restore your data to an alternate system. NOTE: Never restore your data over existing production data. In many instances, it is advisable to work with your network vendor or cloud provider to establish a satisfactory method of testing the validity and completeness of your data. However, depending on the sensitivity of your data or the quantity of data you manage, it may be in your best interest (not to mention the best interest of your customers, shareholders and the general public) to work with a team of disaster recovery experts.
It’s time to start thinking about what your data is worth to your organization and what would happen if you were to lose this data to a cybercriminal. I would also encourage you to download your free copy of our whitepaper, Cybercrime: The Invisible Threat That Haunts Your Business, to learn more.
You can also email Rea & Associates for answers to your questions about Ransomware, cybersecurity and how you can keep your data safe from hackers.
By Travis Strong, CISA (Wooster, OH)
Click here
to download the
free whitepaper
